What is Mobile Device Management?
The shift to remote work in recent years and especially since the start of the pandemic means more mobile devices than ever are accessing corporate networks. Unmanaged mobile devices can create significant security risks, however.
Unmanaged devices can also lead to slowdowns in productivity and logistical friction.
Businesses, as a result, turned to mobile device management (MDM) to manage devices no longer within the traditional perimeter.
MDM wasn’t new when the shift to remote work started, but it went from optional to a necessity.
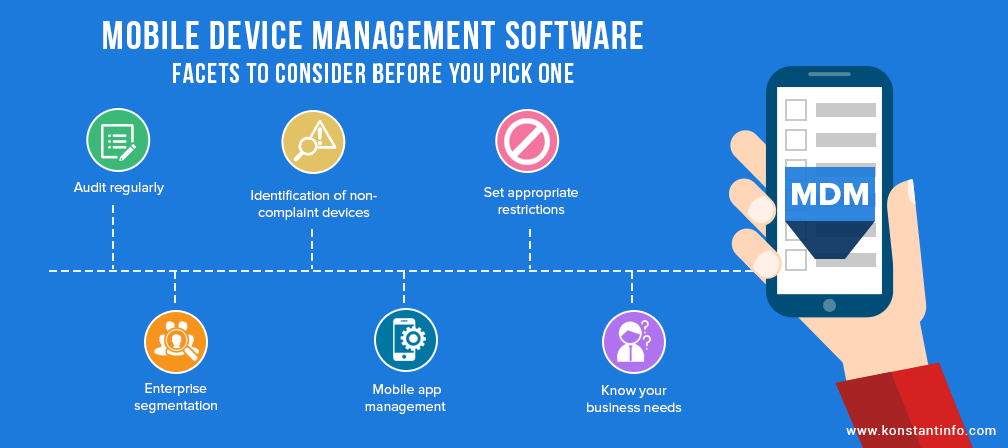
Below are key things to know about MDM and what it can encompass.
Objectives of Mobile Device Management
BYOD, remote, and hybrid work environments often have MDM-related needs that include the following:
• Consistency: BYOD environments have a lot of different types of devices. There need to be standards that take into account these distinctions. Companies should look for MDM solutions that let their IT admin teams keep functionality and security consistent across devices.
• Reporting: As the number of devices accessing a network grows and that growth is often occurring in unsupervised environments, employers need a centralized way to see and monitor the devices. An MDM solution should provide that required visibility.
• Updates: Software that isn’t updated and patched is one of the biggest reasons for security breaches leading to compromised data. MDM solutions should enable you to track unpatched software through device visibility.
• Security: In a BYOD environment, there is an inherent lack of supervision contributing to security problems. MDM solutions add additional layered security to help if your company is BYOD or remote. Particular security features you might find in an MDM solution include Multi-Factor Authentication (MFA) and disk encryption. Another security feature that we talk more about below is the ability to lock and wipe devices remotely. Many MDM tools will let you take these actions if a device is lost or stolen.
• Onboarding and offboarding solutions: MDM solutions can and should make onboarding and offboarding simpler for IT admins. MDM solutions can reduce the physical touchpoints needed to enable longer-term remote work and quickly offboard employees when necessary while reducing security risks that can come with doing so.
The Basics of Mobile Device Management
MDM is a type of security software that allows IT departments to enable security monitoring and manage end-user mobile devices.
There are different types of MDM, each having its own general name. These solutions include:
• Basic MDM: This, as you might guess from the name, is the simplest type of MDM, which lets you view, verify and control any devices on the network. That might mean that you’re able to configure device settings and monitor activity. You may also be able to lock and wipe devices. Basic MDM is pretty standard in remote work environments, but it’s often the only method used for device management. Best practices call for the combination of MDM with other approaches for more secure and strategic outcomes.
• Mobile Application Management (MAM): MAM goes beyond just focusing on devices. The focus is instead extended to applications on those devices. With control over applications, there are security benefits. One example of MAM in action is the implementation of MAM for configuring email application security settings on an employee device. With MAM, IT admins can have security management control over certain apps without affecting others.
• Enterprise Mobility Management (EMM): A combination of basic MDM and MAM, EMM helps IT admins have comprehensive control over devices and what’s on them. With EMM, companies could theoretically encrypt a device and create phishing filters on the email application for corporate emails. EMM can also help if employees lose their devices. IT could go in with EMM and then lock the device and wipe the contents of apps related to the business.
• Device management point solutions: Some companies utilize what are called device management point solutions. This happens because as different needs arise, often due to the changing world brought about by the pandemic, companies develop solutions to address each. Then, companies are using a variety of solutions to address each of their own needs as they occur. The problem here is that if you’re an employer, you’re spending money on multiple solutions. There can also be challenges with integrations between these different solutions. It’s often better to choose something for centralized access management.
With the above in mind, where do you start? The best thing to do is explore an integrated device and identity access management solution. You’ll then have a method for user management and endpoint management to prevent the silo of data.